Researcher 'accidentally' stops spread of 'unprecedented' global cyberattack
The cyberattack hit hundreds of thousands of computers in 99 countries.
— -- A British researcher unexpectedly found and activated a "kill switch" to an "unprecedented" ransomware cyberattack that hit hundreds of thousands of computers around the globe at hospitals, government offices, transportation systems and major companies, including FedEx.
But even with the spread of the malicious software at least temporarily halted, researchers warned that another cyberattack could be imminent and the next one could target the United States.
"Currently the spreading of the ransomware is slowed down dramatically because a researcher found a logic bug in the malware, not because the companies around the world are having good security practice," Matt Suiche, founder of Comae Technologies, a cybersecurity company in the United Arab Emirates, told ABC News on Saturday.
Suiche said the cyberattackers could soon release a new update to the malware, making it more robust and resuming the global infection.
"I'd even say this update probably already happened," he added.
FedEx, other US companies targeted
FedEx was among the many companies worldwide hit by the sophisticated cyberattack that used leaked tools of the U.S. National Security Agency.
A FedEx spokesperson confirmed to ABC News that the U.S.-based international shipper is among the victims of the global cyberattack.
“Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware,” the spokesperson said in a statement. “We are implementing remediation steps as quickly as possible. We regret any inconvenience to our customers.”
Ryan Kalember, a senior vice president at the cybersecurity firm Proofpoint, told ABC News he is aware of other U.S.-based companies who were affected but have not spoken publicly. He said the virus spread rapidly, making it difficult to identify “patient zero” and attribute the cyberattack to a particular hacker group.
Computer networks attacked in 99 countries
The unidentified attackers targeted networks in North America, Europe and Asia, seizing control of computers in dozens of countries by infecting them with malicious software and restricting access until a ransom is paid. Cybersecurity firm Avast said it has detected more than 75,000 so-called ransomware attacks in 99 countries.
"According to our data, the ransomware is mainly being targeted to Russia, Ukraine and Taiwan, but the ransomware has successfully infected major institutions, like hospitals across England and Spanish telecommunications company, Telefonica," Avast said in a statement.
Tyler Wood, a former top official of the U.S. Defense Intelligence Agency who now works for a major telecommunications firm, told ABC News the forensic work to identify the perpetrators may take some time, and it could be a private attacker or a state.
Ransomware attacks are typically carried out by criminal groups, but officials said they cannot rule out anything while investigations remain ongoing.
'Unprecedented' international cyberattack
Europol, the European Union’s law enforcement agency, said the cyberattack has reached "an unprecedented level." The agency said its European Cybercrime Center is working closely with affected countries, cybercrime units and key industry partners to mitigate the treat and assist victims.
"The recent attack is at an unprecedented level and will require a complex international investigation to identify the culprits," Europol said in a statement Saturday
The U.S. Department of Homeland Security said in a statement Friday that it is "aware of reports of ransomware affecting global entities."
Future cyberattacks could be far worse, expert says
Ori Eisen, founder and CEO of cybersecurity firm Trusona, said the scale and speed by which the virus has spread had never been seen before. But the worst is yet to come, he said.
"This is child's play compared to what's ahead," Eisen told ABC News. "The same virus could hit a nuclear power plant, a water bridge, a metro train and the effect would be devastating."
Eisen said the root cause of this threat is simple: static passwords, which are insecure and easily copied. Cyber crooks are taking advantage of simple passwords and computers that aren't patched. And as long as static passwords are being used, Eisen said, the threat will remain.
"The internet is a powder keg that is just waiting for days like this to explode," he told ABC News. "One day, something like this will happen that will change how we think about the internet because it's not safe."
'How to accidentally stop a global cyberattack'
A U.K.-based cybersecurity researcher who cut short his vacation to look into the expanding ransomware attack on Friday happened to come across a "kill switch" in the malware code that stopped its spread, at least temporarily.
The researcher, who tweets and blogs under the name "Malware Tech," recounted the experience in a detailed blog post, "How to accidentally stop a global cyber attack."
"Humorously at this point we had unknowingly killed the malware," the researcher wrote. "Now I should probably sleep."
The NSA 'lost control of its own weapons'
This particular ransomware, called "WannaCry," exploited a vulnerability in Microsoft Windows that was identified by the National Security Agency (NSA) and leaked to the public by the hacker group The Shadow Brokers in April, according to several cybersecurity experts.
“This appears to be the first incidence of the use of an NSA exploit in a broad and far reaching cybercriminal campaign,” John Bambenek of Fidelis Cybersecurity told ABC News.
Following the leak of the NSA tools, Bambenek said he had conversations with high-ranking U.S. national security officials in which he urged them to share information with private vendors so that they could develop countermeasures because the NSA had “lost control of its own weapons.”
“That did not progress rapidly enough, and here we are today,” Bambenek told ABC News. “The NSA can have very smart people finding these vulnerabilities, but not very smart people can start using them to very devastating effect.”
Microsoft rolls out new security update
Microsoft released a patch in March to address this specific vulnerability, but networks that did not adopt it would have remained vulnerable. On Saturday, the American multinational tech company rolled out an additional security update for all customers to further protect Windows platforms.
Microsoft said that users who are running its free antivirus software or have Windows updates enabled are protected. The company said it is also working with customers to provide additional assistance.
"Seeing businesses and individuals affected by cyberattacks, such as the ones reported today, was painful," Microsoft said in a statement Friday. "Microsoft worked throughout the day to ensure we understood the attack and were taking all possible actions to protect our customers."
One U.S. senior official told ABC News that “American companies may fare better than those overseas because they are better at cyberhygiene.” In many cases, the official said, cyberattacks have been successful because they are against pirated or unauthorized copies of Microsoft Windows, which cannot be easily patched to fix the vulnerability.
United Kingdom reels from cyberattack
Some of the first reports of ransomware attacks on Friday emerged from England, where hospitals run by the country's publicly-funded health care system were targeted. The malware locked computers and blocked access to patient files.
As of Friday afternoon, 16 National Health Service (NHS) facilities reported that they were affected by the cyberattack.So far, there's no evidence that NHS patient data in the United Kingdom has been stolen.

NHS Digital, the body of the Department of Health that uses information and technology to support England's health care system, said it is working closely with the National Cyber Security Center and other agencies to fix the damage.
"We are continuing to work around the clock to support NHS organisations that have reported any issue due to yesterday's cyberattack," NHS Digital said in a statement Saturday.
Chris Camacho, chief strategy officer at the cybersecurity firm Flashpoint, said healthcare companies are particularly ripe for ransomware attacks because patient records are so critical to care.
“There’s nothing you can do but pay once you’re hit,” Camacho told ABC News. “If you need that data back, you’re going to pay.”
The National Cyber Security Center, part of British intelligence services, said it is working "round the clock" with its partners and experts "to lead the response" to the cyberattacks in the United Kingdom and worldwide.
The cybersecurity agency advised organizations to protect themselves by making sure that security software patches are up to date, computers are running proper anti-virus software and data is backed up on an external hard drive.
Russia digs out from large-scale attack
Russia appears to have been targeted by the ransomware on a particularly large scale, with nearly all of the country's key sectors reporting attempted attacks, including law enforcement, health care, emergency services, telecommunications, finance and transportation.
Still, unlike in the United Kingdom, most Russian entities reported that they successfully repelled the cyberattack.
Russia's Ministry of Internal Affairs released a statement saying just 1,000 of its computers -- around 0.1 percent -- were affected and that they were able to block the malware.

Russia's Ministry of Healthcare and Ministry of Emergency Situations also reported attempted cyberattacks that they were able to fend off.
One of Russia's largest telecom operators, Megafon, said it suffered "quite a large" cyberattack that locked its computers. The company said it managed to eventually unlock the computers Friday night. Russian mobile operator Beeline also confirmed that it was the target of an attempted attack.
Russia's central bank reported that major financial institutions came under attack but have since recovered.
The country's railway operator, Russian Railways, was also attacked and repelled the virus.

Kalember at the firm Proofpoint told ABC News that Russia was particularly vulnerable because many of its networks use older versions of Microsoft Windows.
“This is depressing as a cybersecurity expert,” Kalember said. “The patch has existed since the vulnerability was made public, so if people were applying it, this never had to happen.”
Germany's railway was a victim
German railway company, Deutsche Bahn, confirmed in a statement Saturday that it was among the victims of the global cyberattack.
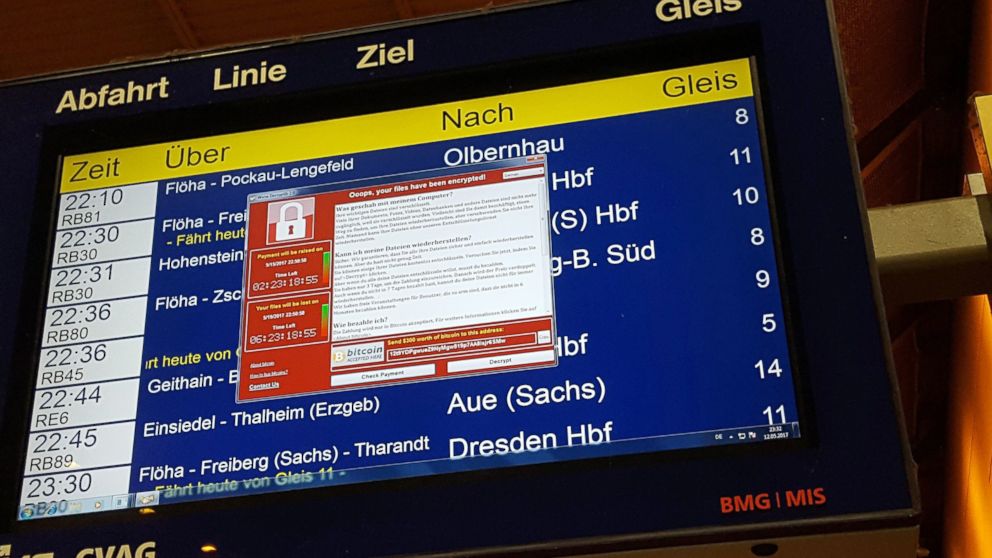
Although there was no impact on actual train services, Deutsche Bahn said departure and arrival display screens at its stations were affected Friday night. Additional staff was deployed to busy stations to provide customers with information, the national railway company said.
Cyberattack cripples carmakers
Major multinational automobile manufacturers, including Japan's Nissan and France's Renault, were also affected.
“Like many organizations around the world, some Nissan entities were recently targeted by a ransomware attack. Our teams are responding accordingly and there has been no major impact on our business. We are continuing to monitor the situation," a Nissan spokesperson said in a statement Saturday.

The cyberattack forced Renault to halt production at sites in France in an effort to stop the malware from spreading, union members told The Associated Press.
Renault officials were not immediately available for comment, according to AP.
ABC News' David Caplan, Maia Davis, Julia Jacobo, Mike Levine, Mike Trew, Devin Villacis and Marcus Wilford contributed to this report. The Associated Press also contributed to this report.



