How Hackers Can Copy Everything on Your Phone
Celeb hacking scandal sheds light on tools hackers might use.

— -- The hacks into the clouds of dozens of Hollywood A-listers, including Kate Upton and Jennifer Lawrence, have shed new light on the methods hackers might use and the tools they have at their disposal.
On the Web forum Anon-IB, a popular image sharing board, users posted what they claimed were stolen, naked photos, and talked about how they got them. They discussed using the ElcomSoft Phone Password Breaker, according to Wired.
The product is just one of many available for sale online.
The company said the product is intended for computer forensics experts and people who need help cracking their own accounts, allowing users to download everything from a cloud account. The end result can be a virtual copy of someone's entire phone. The software starts at $79 and can be purchased from the Moscow-based company's website.
Lizard Squad: Who Is the Group Claiming Responsibility for High-Profile Hacks?
Hacking Victim Turns Tables on Attacker With Bounty
Sony Network Hacked, Exec's Flight Diverted
Robert Siciliano, a McAfee identity theft expert, told ABC News that while the tools are marketed to law enforcement professionals, they were originally geared toward security professionals who are called "ethical hackers."
"These are your white hat hackers, good guys who spend their days looking for vulnerabilities in various networks or devices so they can patch them and update that organization's security posture," Siciliano said.
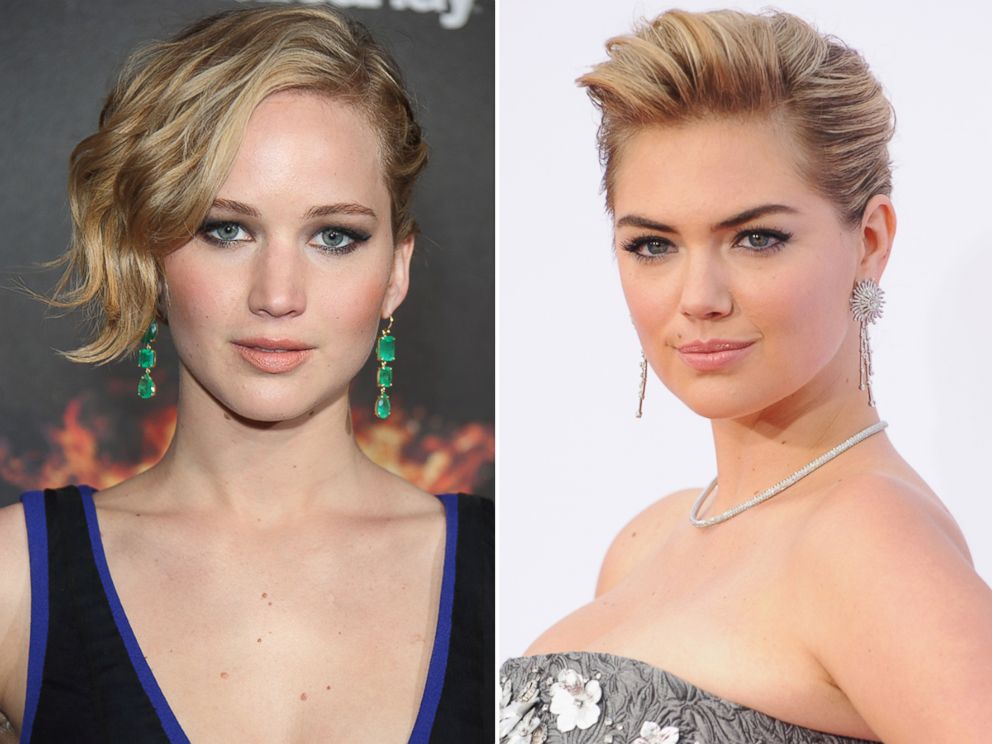
For ordinary civilians, though, it's not just their phones that could be vulnerable.
ElcomSoft also offers software that claims to be able to access someone's Facebook log-in and password information.
"The free Facebook Password Extractor reveals Facebook passwords cached in all popular Web browsers in just a click. Multiple Facebook accounts and latest versions of Microsoft Internet Explorer, Mozilla Firefox, Apple Safari, Opera and Google Chrome are supported," the product description said.
ElcomSoft also offers email and instant messenger password recovery products.
In addition, a Forensic Toolkit product is listed for sale on ElcomSoft's website starting at $1,495. The bundle claims to allow users to acquire bit-precise images of targeted Apple iOS devices in real time.
Olga Koksharova, a spokeswoman for ElcomSoft, told ABC News that limiting access to the software won't prevent hackers from finding a free version somewhere else.
"There are numerous legitimated uses of this software," Koksharova told ABC News via email. "One of them is getting access to your own iCloud information in case you break, lose or somehow damage iOS device and are not going to or cannot buy a new device to restore the data to a new device."
The company said on its website that it "caters to the needs of law enforcement, military and intelligence agencies, supplying a range of forensic products and tools used in criminal investigations."
While Siciliano said this type of software is generally sold with good intentions for commercial use, it could just as easily be used to inflict damage.
"These software programs are no different than a gun," he said. "They can be used for defense or offense. They can be used to kill or to save a life."




