Google Report Reveals 4 Simple Steps Hackers Take to Ruin Your Digital Life
Google report reveals how hackers target, take over and monetize your accounts.

— -- Hackers can get surprisingly close to compromising an individual's account in a matter of a few quick steps, according to a new Google report that reveals the secret playbook used by hackers.
While the attacks are rare, with just nine per one million users reported per day, according to Google, they can be incredibly damaging.
The stealth tactics used by manual hijackers to individually target an account -- as opposed to those who use an automated bot -- can leave personal information and contacts vulnerable and even expose everything inside a victim's bank account, according to the report, which draws from lessons learned from 2011 to 2014.
Google offered a comprehensive look at the inner workings of these hackers -- from a play-by-play of the steps they take to their schedules and the lessons that can be learned.
Phishing
Many victims are lured into a manual hijacker's trap by falling prey to a phishing email.
"It requires less infrastructure than operating a botnet and allows attackers to target specific victims, especially an existing victim’s contacts," the report said.
In many cases, users were sent an email that directed them to a login page that looked legitimate and prompted them to enter their login information. Many of the spoof pages were for well known sites, and left user's email accounts and in some cases, their financial information, vulnerable.
Assess the Value
Of the test email addresses Google used, 20 percent of the accounts were broken into within 30 minutes of hackers getting the login information. Half were broken into within seven hours from the moment the account owners took the phishing bait.
From there, hackers took an average of three minutes to assess the value of the accounts, such as looking for banking details or messages flagged as important, before deciding whether it was worth proceeding.
Monetize
Hackers may have a target's banking information after infiltrating their account -- or they can try to target their contacts for money.
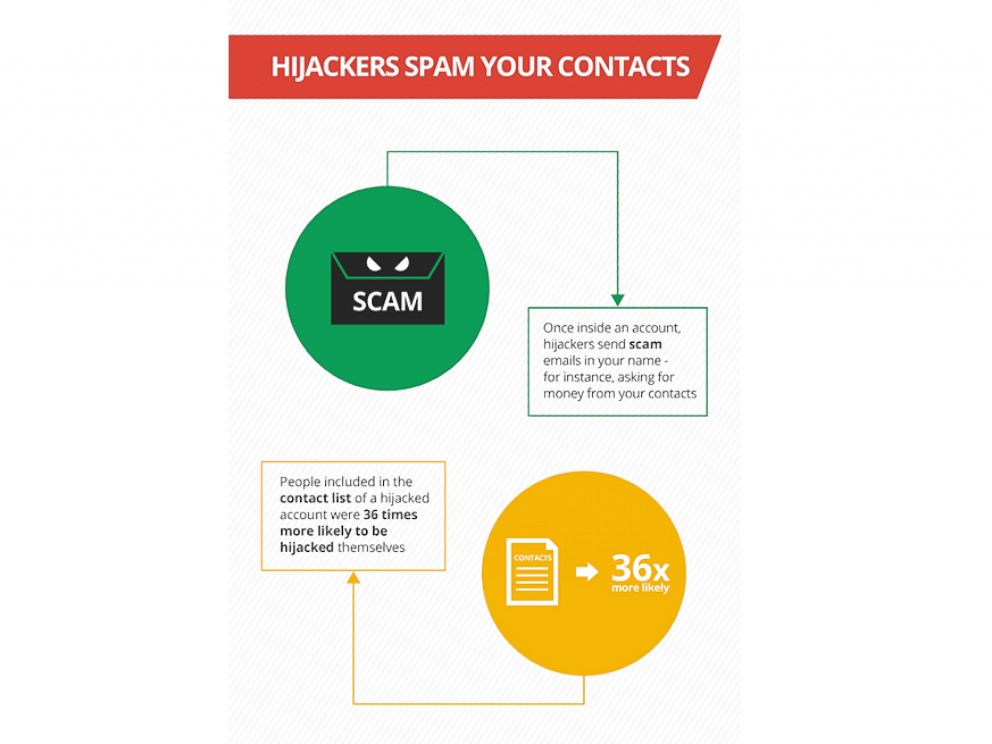
If they decided to proceed, hackers spent an average of 15 minutes looking through a compromised account's emails and figuring out ways to personalize their scams. The most common way was to send a scam email to contacts, detailing a harrowing story such as a mugging while on a vacation abroad.
The emails typically ask for a quick loan to help extricate themselves from the tragic situation. Another commonality: They usually include details such as the user claiming their phone was stolen so the friend receiving the email will not think twice about contacting them to verify the note is legitimate.
Even more frightening, contacts of a compromised account are 36 times more likely to be manually hijacked too, according to Google.
Delay Account Recovery
Holding off the rightful account owner is key to a hacker's success. According to Google, manual hijackers will take steps to lock users out of their accounts for a while so they have time to exploit and monetize the hack.
One way hackers can keep account owners at bay is by changing the password. Sometimes they delve deeper, changing the account recovery options, thus creating a more time consuming process for someone who is locked out to once again gain access to their accounts.




