10 days after ransomware attack, Irish health system struggling
Many hospitals still have no computers a week on.
DUBLIN -- Staff coming into work at several Dublin hospitals on Friday, May 14 found an unsettling sight: Throughout the building, every computer screen was dark.
It was the result of the massive ransomware attack that crippled Ireland's health service's IT systems and that has left most of the country's hospitals without computers for over a week.
The outage has wreaked chaos, forcing the mass cancellation of routine appointments, blocking access to patients' records, hobbling testing and some key treatment services, including for cancer patients.
It will likely be weeks before the systems are fully recovered, and each day it continues, more of a backlog is created, which puts pressure on medical workers. Meanwhile, the criminal gang behind the attack is threatening to release patient data it stolen during it.
"It's just such a mess. There's just people running around. It's totally chaotic," one doctor from a Dublin hospital told ABC News, speaking anonymously because of hospital rules restricting staff from talking to media.
The cyber attack that struck Ireland was the worst in the country's history, and it happened just after the cyber attack on the Colonial Pipeline in the United States. The two ransomware attacks have thrust cybercrime to the front of international attention in a way that a long list of previous ruinous attacks perhaps haven't. The American pipeline attack has already prompted President Joe Biden to sign a new executive order aimed at strengthening the U.S.' cyber defense.
"These are going to be two big moments in the fight against ransomware," said Brian Honan, a cybersecurity consultant in Dublin.
A health system crippled by a cyberattack during a pandemic sounds like something out of a disaster movie. But that is the improbable reality Ireland's officials and medical workers have been dealing with for over a week. With the COVID-19 pandemic "everything is stretched at the minute anyway," a doctor at another big Dublin hospital said on condition of anonymity. "It's just an extra stretch that we didn't need."

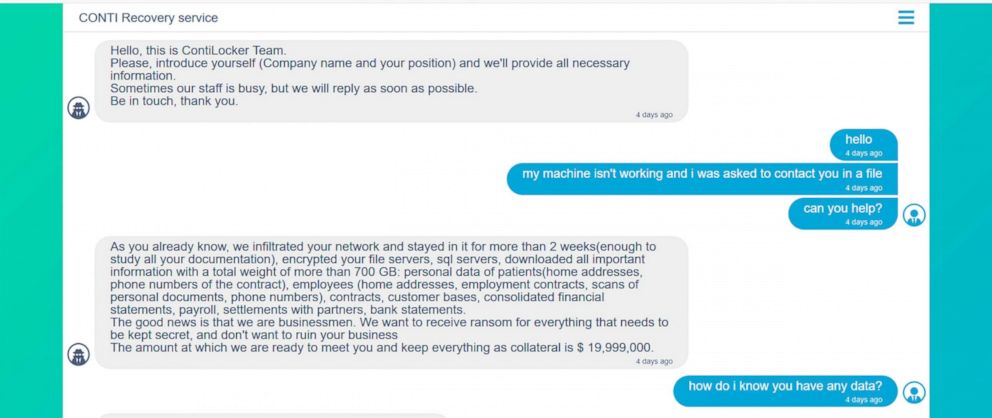
The attack began in the early hours of the morning on Friday, May 14, and targeted the systems of Ireland's Health Service Executive (HSE) as well as many hospital servers. The hackers would later claim they had spent two weeks in the HSE's systems before launching the attack and claimed to have encrypted and stolen 700GB of data.
The impact has been sprawling and likely dangerous, far beyond postponed routine appointments or added paperwork.
One of the biggest challenges is medics now have limited or no access to patients' records, meaning they have limited knowledge of their medical histories. Lab results now also have to be printed and hand-delivered. That has slowed lab testing significantly and forced the health service to ration blood testing in many places, reserving it only for urgent cases.
In hospitals, everything now has to be tracked again on paper. Labels printed onto samples and blood transfusions are now written by hand. Staff have been advised to not even turn on their computers.
"The opportunity for error is massive. I mean things like people getting the wrong blood transfusions, samples being sent under the wrong patient's name," one of the doctors at a Dublin hospital told ABC News.
A psychiatrist working on a community mental health team also speaking on condition of anonymity described struggling to discover what medication a patient was on without access to their records.
"I reviewed one patient and needed to make a decision about whether to change medication. He didn't know what he was on, and I couldn't verify that information," the psychiatrist said, adding that a process that should have taken minutes took days.
One of the most serious impacts has been on medical imaging. The software used for sharing X-rays and CT scans is down, meaning in most hospitals it has become impossible to send imagery between departments or between hospitals. Doctors were forced to go in person to X-ray machines or else rely on written descriptions. They have, in some cases, resorted to taking photographs of scans with their phones to send to each other via messaging apps like WhatsApp, something forbidden by the health service because of privacy laws.

"It's that or you accept that the patient receives substandard care," one doctor said. "It's a nightmare."
Doctors are also unable to look back at any previous scans, making comparison impossible. When treating cancer patients, for example, doctors are currently unable to see how the cancer may have spread.
Radiation therapy for cancer patients is also largely suspended because computers are needed to control dosing.
The disruption means many hospitals and clinics have had to limit their services to urgent cases only. Referrals are also affected because they have to be done by phone or post.
Doctors speaking to ABC News said they are finding ways to treat patients through the disruption and working harder to fill the gaps. But they fear it's inevitable that diagnoses will be missed and treatment for patients will suffer as a result of the diminished systems.
Some expressed frustration that there have been so few safeguards within the hospital systems to protect them, noting that many hospitals are still equipped with old computers, many running only Windows 7 – a program for which Microsoft stopped providing security support in January 2020.
The ransomware used in the attack is well-known, named Conti. It was developed by a cybercrime gang thought to be based in Russia, which rents it out to affiliates. The gang sought to communicate with the health service through a chat, publicly reviewable on the Dark Web. Messages posted to the chat show the gang demanded nearly $20 million as a ransom and also threatened to start selling data stolen during the attack, a tactic known as "double extortion."
Ireland's government has refused to pay the ransom and began the grueling process of recovering the systems, calling in the cybersecurity companies FireEye and McAfee to assist.
That process was aided when the gang took the surprising step of providing a decryption tool to the health service for unlocking the files encrypted by the ransomware. The criminals gave the key a week into the disruption, but did not drop their threat to release the stolen data if the ransom wasn't paid.
Ireland's authorities, after testing it, found the tool was genuine but warned it worked badly and slowly and said it was not a "silver bullet." In a statement over the weekend, the government said "very steady progress" was now being made, in part thanks to a re-engineered version of the tool, but cautioned it could still likely take weeks to recover systems.
"This is like, somebody mugs you, steals your money, beats you up and then comes back with your empty wallet," Honan, the cybersecurity consultant, told ABC News. "It's an empty gesture really. The damage that has been caused by this is already immeasurable. I think the general thoughts are that it is a PR stunt."
Honan believes the gang likely realized Ireland wouldn't pay the ransom and was making progress in recovering its files and so they made a cynical decision to hand over the key. He noted that the Colonial Pipeline paid $5 million for a decryption key that worked so slowly the company had to continue recovering its systems from backups anyway.
A memo sent to staff on Monday by Children's Health Ireland that manages several children's hospitals in Dublin said that they were still in just the first phase of recovery and that services would remain restricted to urgent cases until next Friday, May 28. The organization told staff that in the next few days some large adult hospitals in Dublin would likely get their systems back online because they were not as badly affected.
The ransomware gang had set Monday as the deadline before they would start selling the health service's stolen data. Ireland's prime minister, Michael Martin, on Monday said so far there was no sign the criminals had done so on a large-scale, but authorities still expect it will happen. Irish police have warned that could mean repeated waves of fraud linked to the data.
"Cybercrime is not a victimless crime," Honan said. "It's not a crime against a computer. This is hurting people."




